
The boundary subsystem is the subsystem at the interface between the system and its environment that recognizes and holds together the components which make up the system, protects them from environmental stresses and internal disruptions, and excludes or permits entry to various sorts of matter-energy and information. [New elements in bold type.]If we allow that the boundary does not necessarily lie at the perimeter of the system but is found wherever there is an interface between the system and its environment (i.e., between self and other), the immunity processes are clearly a function of the boundary subsystem. Nevertheless, as the controversy is not fully resolved, I will continue to refer in this paper to an immunity subsystem that includes these processes.
Table 1. THE 19 CRITICAL SUBSYSTEMS OF A LIVING SYSTEM

Figure 1. Interrelationships of 19 Critical Subsystems
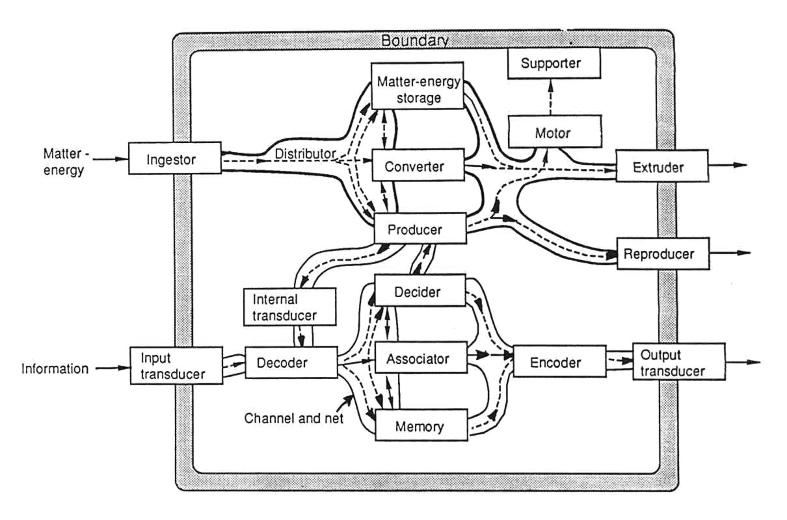
Table 2
| What Are the Characteristics of Life? |
|---|
| 1. Composed primarily of protoplasm |
| 2. Environment supports it |
| 3. Has a template (genes, charter) |
| 4. Is an open system |
| 5. Purposefully acts to: A. Maintain itself against entropy B. Actualize its potential C. Propagate itself |
| 6. Requires 19 critical subsystems |